Defense in depth defined

Defense in Depth (DiD) is an approach to cybersecurity in which a series of defensive mechanisms are layered in order to protect valuable data and information. If one mechanism fails, another steps up immediately to thwart an attack. This multi-layered approach with intentional redundancies increases the security of a system as a whole and addresses many different attack vectors.
How defense in depth works
No organization can be ever be fully protected by a single layer of security. Where one door may be closed, others will be left wide open, and hackers will find these vulnerabilities very quickly. However, when you use a series of different defenses together, such as firewalls, malware scanners, intrusion detection systems, data encryption and integrity auditing solutions, you effectively close the gaps that are created by relying on a singular security solution.
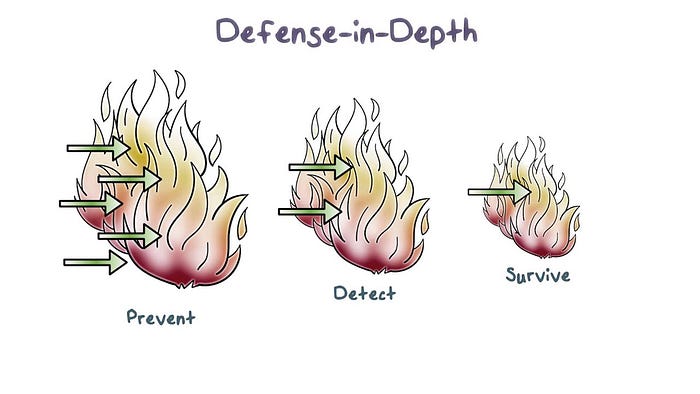
Elements of defense in depth
Network Security Controls
- The first line of defense when securing a network is the analysis of network traffic.
- Firewalls prevent access to and from unauthorized networks and will allow or block traffic based on a set of security rules.
Antivirus Software
- Antivirus software is critical to protecting against viruses and malware.
- Many variants often rely heavily upon signature-based detection.
- While these solutions offer strong protection against malicious software, signature-based products can be exploited by intelligent cybercriminals.
Analyzing Data Integrity
- This is a mathematical representation of a file that shows the frequency of its use, If an incoming file is completely unique to the system it may be marked as suspicious. Data integrity solutions can also check the source IP address to ensure it is from a known and trusted source.
Behavioral Analysis
- File and network behaviors often provide a warning while a breach is in progress or has occurred.
- If behavioral analysis is activated it means the firewall or intrusion protection solutions have failed
- It can either send alerts or execute automatic controls that prevent a breach from continuing any further

